 Unfortunately, as this pandemic continues to unfold, we will see more cybercriminals taking advantage of the situation. Everyone is affected in one way or another, this includes hackers. So, in order to continue to double our cybersecurity efforts, it may be a good time to enable multi-factor authentication (MFA) on all available online accounts. When it comes to protecting your critical corporate data from unauthorized hackers and cybercriminals, passwords are typically the weakest link. That’s why MFA has become the identity and access management (IAM) standard for preventing unauthorized access.
Unfortunately, as this pandemic continues to unfold, we will see more cybercriminals taking advantage of the situation. Everyone is affected in one way or another, this includes hackers. So, in order to continue to double our cybersecurity efforts, it may be a good time to enable multi-factor authentication (MFA) on all available online accounts. When it comes to protecting your critical corporate data from unauthorized hackers and cybercriminals, passwords are typically the weakest link. That’s why MFA has become the identity and access management (IAM) standard for preventing unauthorized access.
What exactly is Multi-Factor Authentication (MFA) you ask?
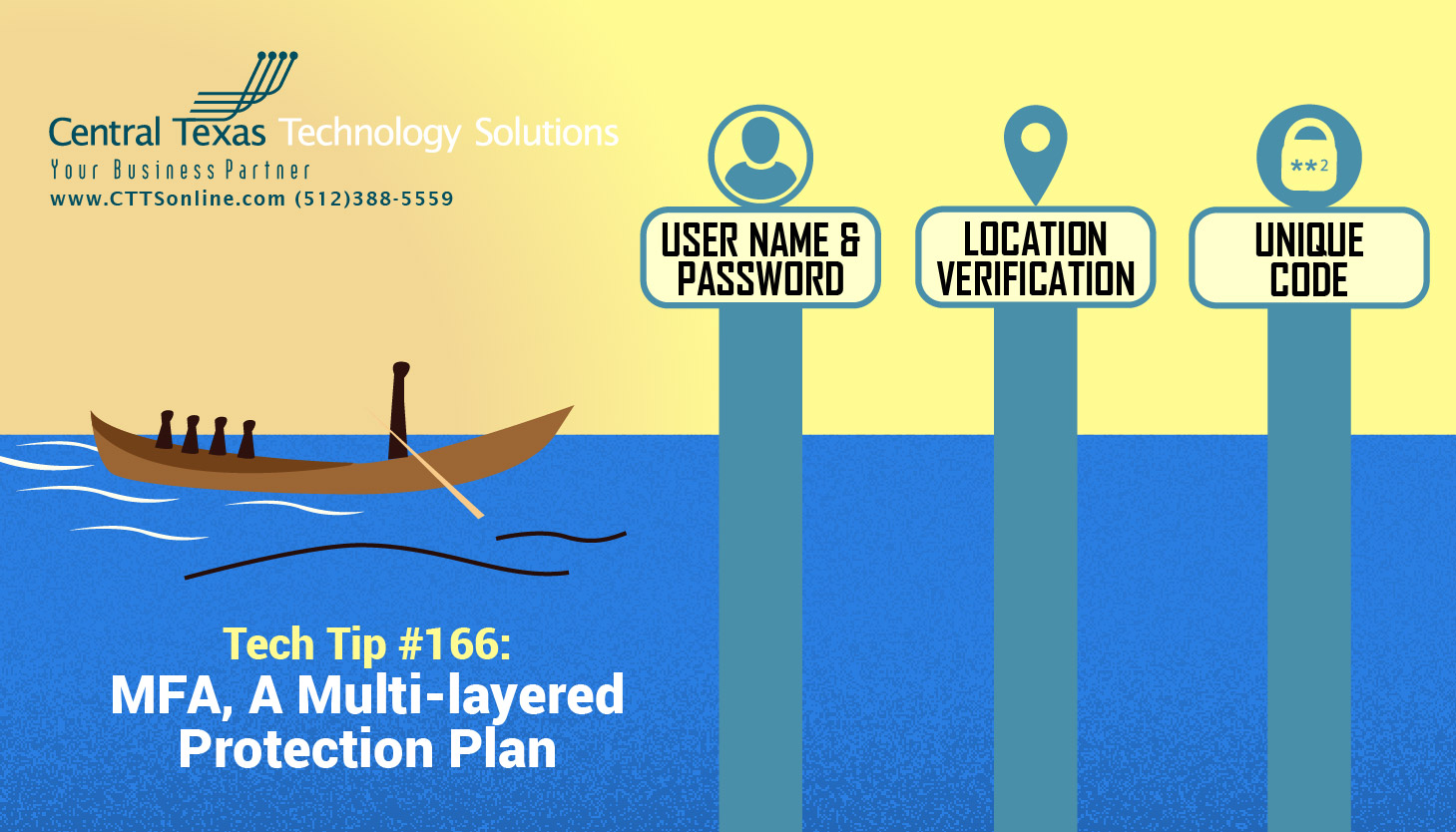
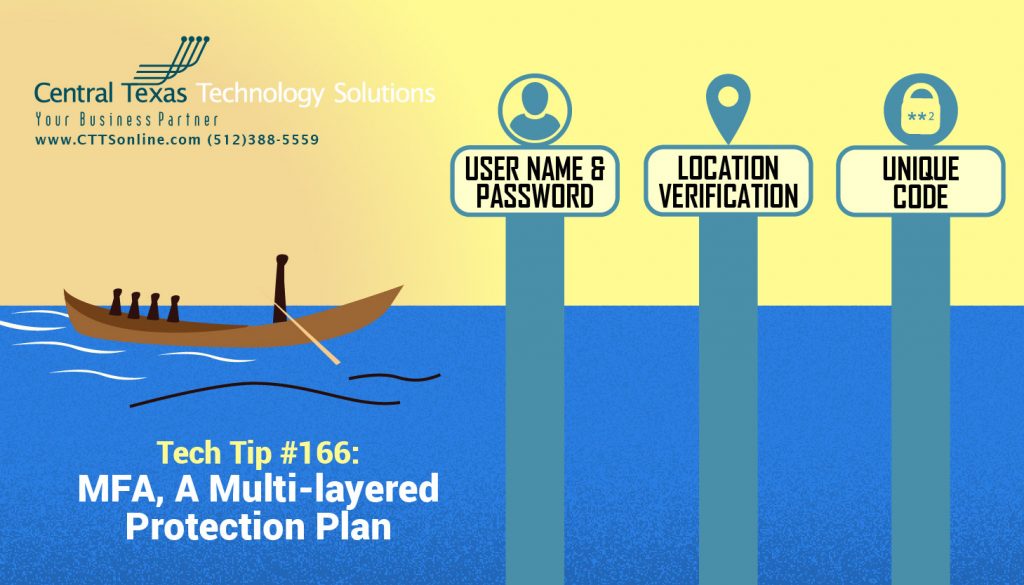
This security enhancement allows you to present multiple pieces of evidence – your credentials –to verify the user’s identity for a login or other transaction. It is a method of confirming users' claimed identities by using a combination of different factors. A multi-layered defense makes it more difficult for unauthorized persons to access your computing device, network or database. If one factor is compromised or broken, the attacker still has at least one more barrier to breach before successfully breaking in.
MFA is just another way to confirm your identity. Say you're applying for a job and they ask you for two types of identification, it’s the same concept but in a more technologically advanced form.
For this to work, you'll need to either use your phone to decipher a QR code, receive a text or use an app that then gives you a random code that will reset after a certain amount of time if unused. You can then enter the code and securely gain access to your account or application. This is on top of your normal username and password. MFA is an extra layer of protection so that if someone does gain access to your credentials through the dark web or by other means, they'll still need that additional code to get in.
Now that we understand a bit about what MFA is and why we need MFA in our business and personal lives, let talk about the different types of authentication.
There are 4 possible factors in a multi-factor authentication scheme that may include something you:
- Have - a physical object such as a USB stick with a secret token, a bank card, a key, etc.
- Know - like a password, PIN, TAN, etc.
- Are - a physical characteristic of the user (biometrics), such as a fingerprint, eye iris, voice, typing speed, pattern in key press intervals, etc.
- At - a GPS location-based identity or connection to a specific computing network.
Check your application security settings now to see if MFA or two-factor authentication (2FA) is an option for your cybersecurity.
Would you like assistance or more information about securing your company data and network? Give CTTS a call today, we're happy to answer any business technology and security questions you may have and can even offer you a free technology assessment to see where your business currently stands, give CTTS a call now:(512) 388-5559.

By Ramon Kreher
Desktop Support Technician
Central Texas Technology Solutions
